The Apple AirTag smart tracking device was recently launched by the company. But just this last weekend, a German security researcher has apparently managed to jailbreak the smart tag.
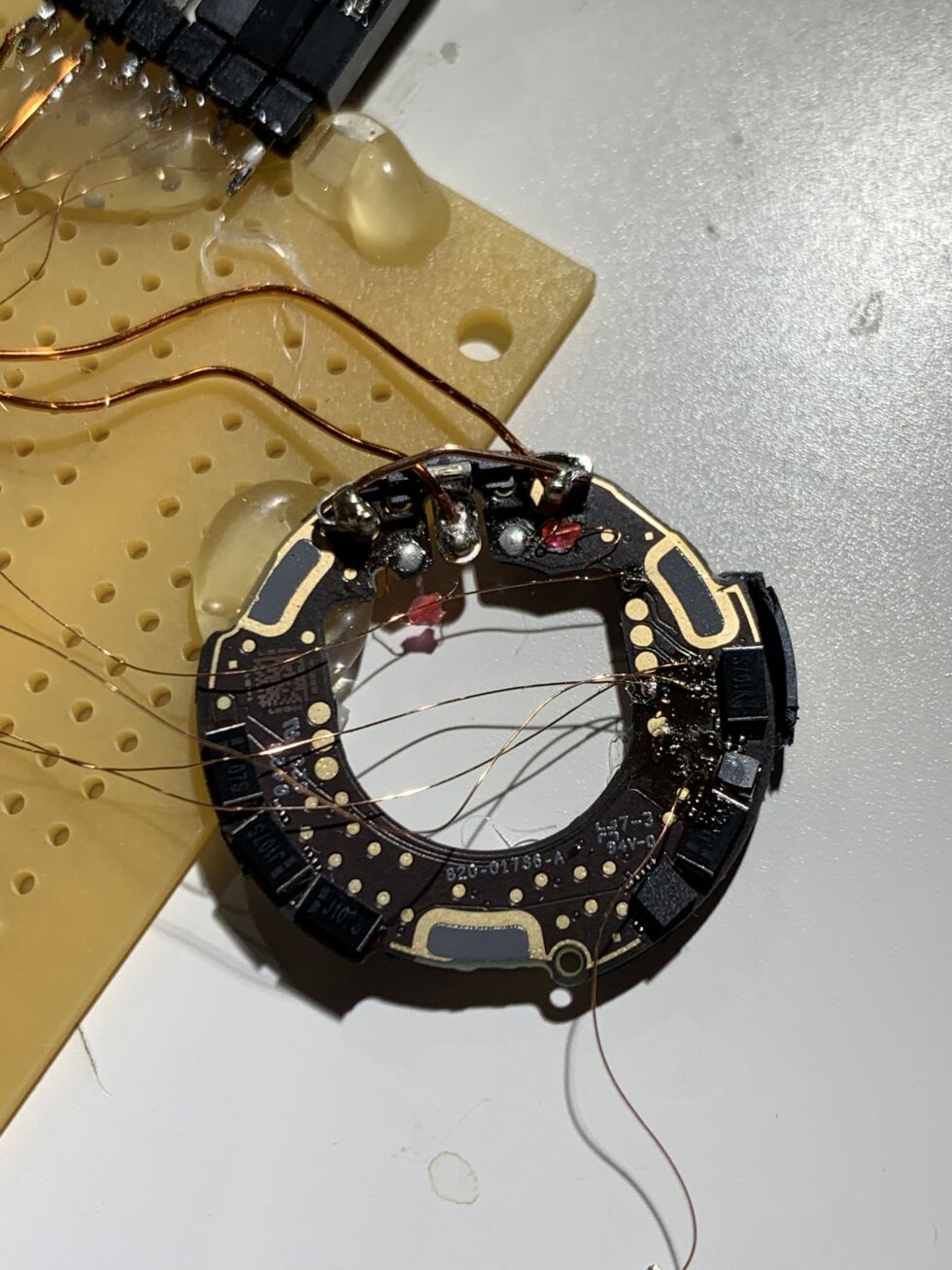
According to a ArsTechica report, Stackmashing declared that the attempt to jailbreak the AirTag was successful. For those unaware, the new product from the Cupertino based giant is a small object tracker that can help users locate their key chains, bags, wallets, and more. And now, the security researcher stated that he was successful in breaking into, dumping, and reflashing the microcontroller of the company’s new AirTag. As per the report, breaking into the microcontroller basically implied that the researcher was able to both device how the device functions (by analyzing the dumped firmware) and also reprogram the gadget to do things it was not programmed for in the first place.
This was demonstrated by Stackmashing by having the AirTag be reprogrammed to pass a non Apple URL while in the Lost Mode. This mode is the state that the device enters into when the user starts searching for the object the AirTag was attached with. So when someone with an NFC enabled smartphone finds the AirTag, they can tap it and receive a notification with a link to found.apple.com. This link helps the person who found the device to contact the owner.

But Stackmashing was able to replace this link with a URL of any kind after breaching the microcontroller. In the demonstration, the security researcher managed to add a modified URL into the AirTag that would directly lead to the stackmashing.net website. While this doesn’t directly imply a grave security breach, it does imply the possibility of targeted malware attacks that could be made possible.
RELATED:
- Apple may launch iPhones with in house 5G Modems by 2023: Kuo
- Apple iPhone 12 production in India drops more than 50% due to COVID-19
- Apple AirTag iFixit Teardown: ‘Impressively Compact’ Design compared to Galaxy SmartTag







