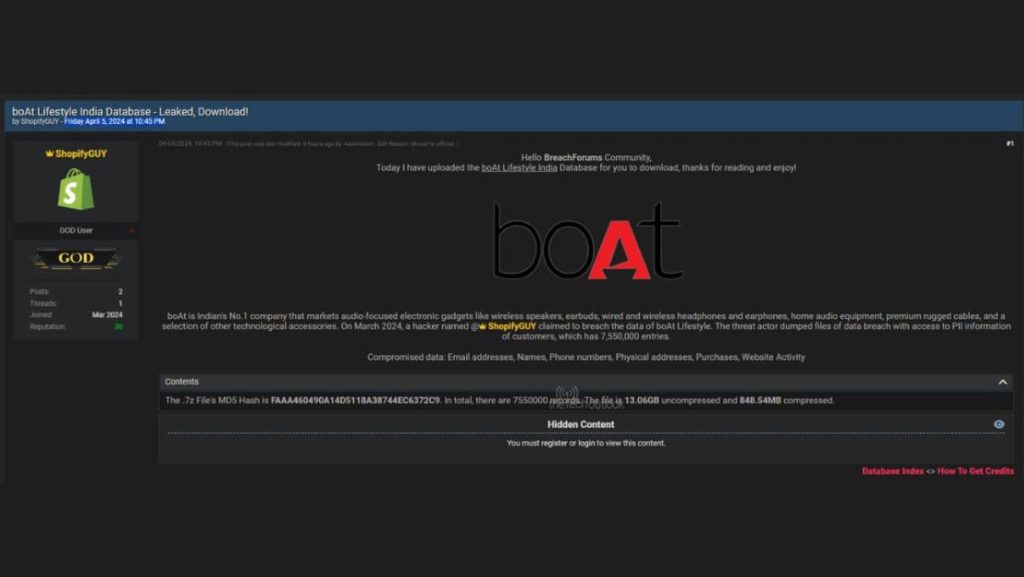
Indian electronics manufacturer boAt has experienced a major data breach, compromising the personal information of an estimated 7.5 million customers.
The breach was first reported by Forbes India and reportedly includes sensitive Personally Identifiable Information (PII) of users such as names, addresses, phone numbers, email addresses, customer IDs, and more.
The breach is said to have occurred on April 5, 2024. A hacker operating under the name “ShopifyGUY” has claimed responsibility, dumping roughly 2GB of stolen customer data onto a dark web forum.
Security experts warn that those impacted by the breach face increased risks of identity theft, financial fraud, and phishing attacks. The stolen information could enable threat actors to access bank accounts, make fraudulent purchases, or launch targeted scams.
“Loss of customer confidence and potential legal repercussions” could be the consequences for boAt, according to cybersecurity threat researcher Saumay Srivastava. “The major implications make it even more essential to implement adequate security practices,” he adds.
NetEnrich senior threat analyst, Rakesh Krishnan, believes the hacker likely gained access to the data well before its release on the dark web forum. His opinion is that the leak is intended to establish the hacker’s reputation within the cybercrime community since the leaker’s profile is relatively new and only has this leak under his name.

Security Brigade founder Yash Kadaki said “The data is available for eight credits on some forums, so literally, it costs two euros to buy the data. It’ll probably be available for free in a few days on Telegram. This data will be used by a lot of scammers for different phone and email scams.”
Scammers might frequently use such data for fraudulent email and phone calls. So boAt must take sufficient action in response to the breach. However, the company has not yet publicly acknowledged the data breach or provided guidance to affected customers.
Related:
- Boat Nirvana Eutopia headphones with spatial audio & 3D head tracking launched
- Boat Airdopes Supreme TWS earbuds with 50-hour battery life & in-ear detection launched
- boAt Stone Spinx Pro Now Available For Purchase In India At Rs 2,999
- Get latest Oneplus 12 Phone for $699 on Geekwills
- Get $100 Off on Vivo X100 Pro at Giztop
- Get the Realme GT5 Pro phone on Giztop for $599
- Xiaomi 13 Ultra Premium Camera Phone is now only $799







